« Give me delightful products and I’ll give you all my data. »
~Unknown
Technology in 2020 took a massive turn from being mankind’s servant to becoming, nowadays, its master. We can safely say that one of our biggest addiction is our cellphone. However, little do people know how much private information is being collected by our devices every second. According to a post featured on the New York Times, approximately 50 billion location pings are held in one huge dataset that contains all the information our phones transfer.
Thus two problems reside; the first being the actual collection of data and privacy invasion, the second resides in the security when it comes to this collected data for it not to be published.
Then we ask ourselves: Is privacy dead?

The Study
This study is based on free datasets available online for the public ranging between the years 2008 to 2014. It is primarily based on the US region and covers the following:
- The numbers affected.
- The affected organization types.
- The type of breaches.
- The source of compromised data.
- The methods used.
- Top famous passwords.
The Evolution of Data Breaching
The graph below illustrates the number of individuals affected by data breaching in the USA between the years 2008 and 2014
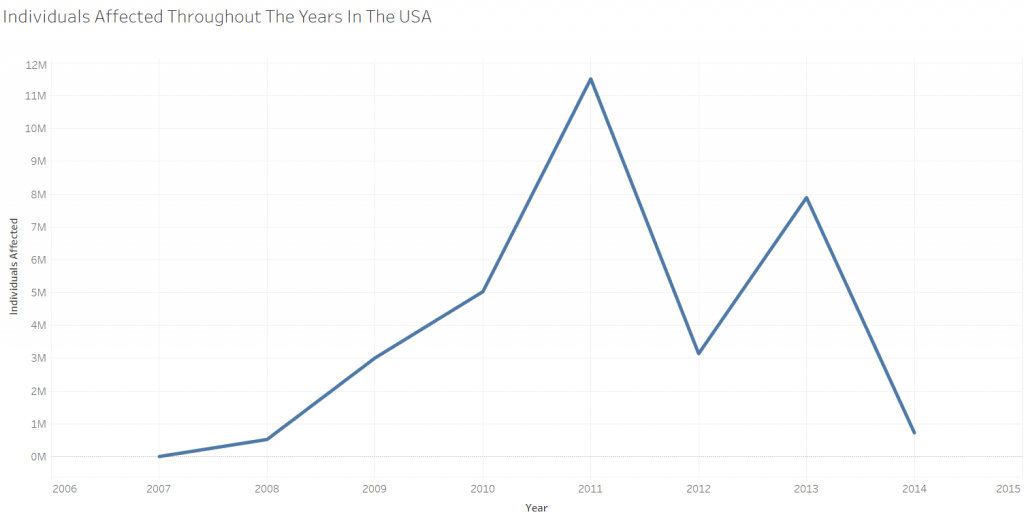
Data Source: https://www.kaggle.com/alukosayoenoch/cyber-security-breaches-data
The years 2011 and 2013 have shown a spike in the world of data breaching. In fact, in 2011, the famous PlayStation Network hack has affected around 77M users compromising their information, including bank accounts, along with notable Epsilon hack in which the Irish Computer Society stated that between 60 and 250 million accounts were jeopardized. Moreover in 2013, according to an article found on CSO, both Adobe and Myspace have reported data breaches reaching around 153 million and 360 million accounts respectively. The article also states that around 3 billion Yahoo accounts were compromised between the years 2013-2014.
Even though the numbers in 2013 seem higher than the ones in 2011, the graph shows the number of people affected by the breach. And since most Yahoo and Myspace accounts were considered obsolete at that time, as the majority of people switched to Google and Facebook, this would explain the graphs’ appearance.
A Geographic Approach
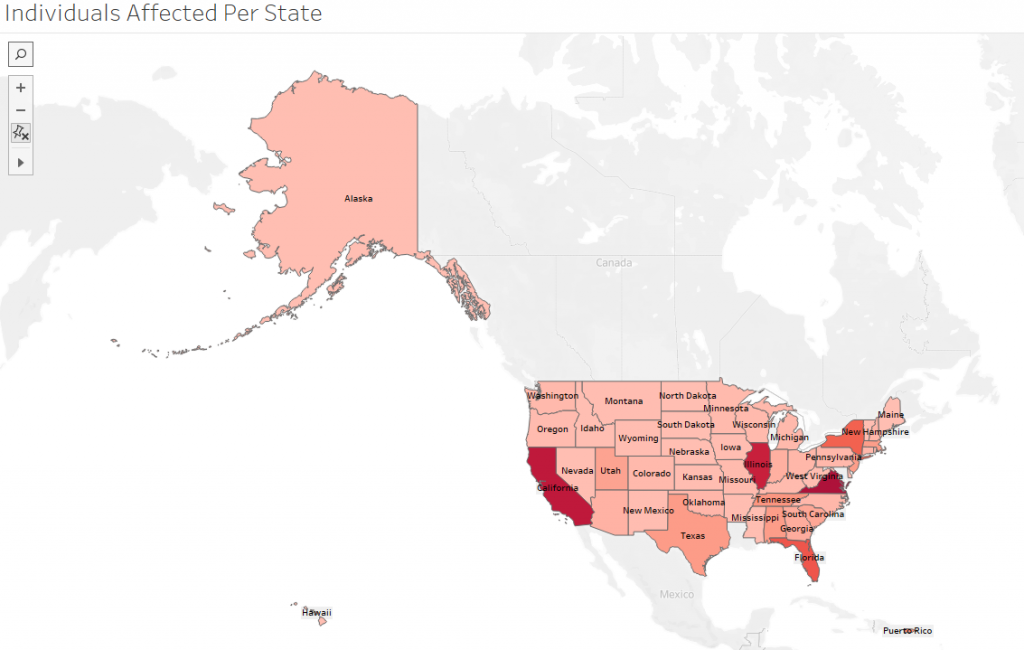
Data Source: https://www.kaggle.com/alukosayoenoch/cyber-security-breaches-data
The graph above represents the most affected states in the US region. California, Illinois, and Virginia rank highest, followed by Florida and Texas.
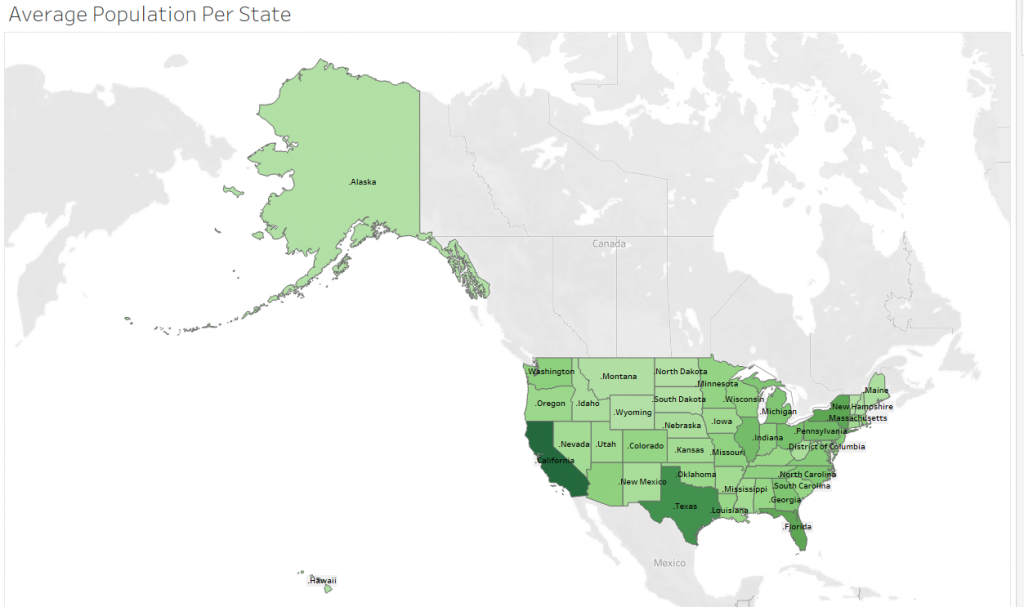
Data Source: https://www.census.gov/data/datasets/time-series/demo/popest/2010s-state-total.html
These states (along with others) happen to be some of the heavily populated states in the United States, which explains the attacks’ dispersion.
The Targets
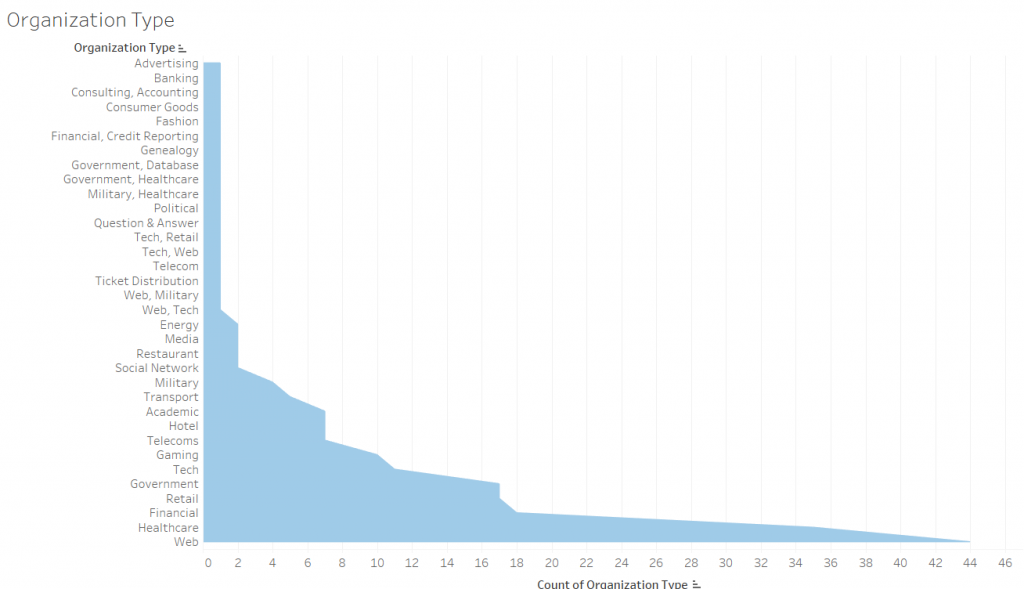
Data Source: https://www.kaggle.com/rileyrinidad/cyber-attacks-20102018#cyberattacks.xlsx
According to this graph, the top 3 most targetted organizations are the Web, Healthcare, and Financial fields.
As for the Web field ranking first, this information was quite expected.
Breaching ≠ Hacking
A common mistake is to confuse data breaching and hacking.
A data breach is a security incident in which information is accessed without authorization. Whereas hacking is a subtype of data breaching.
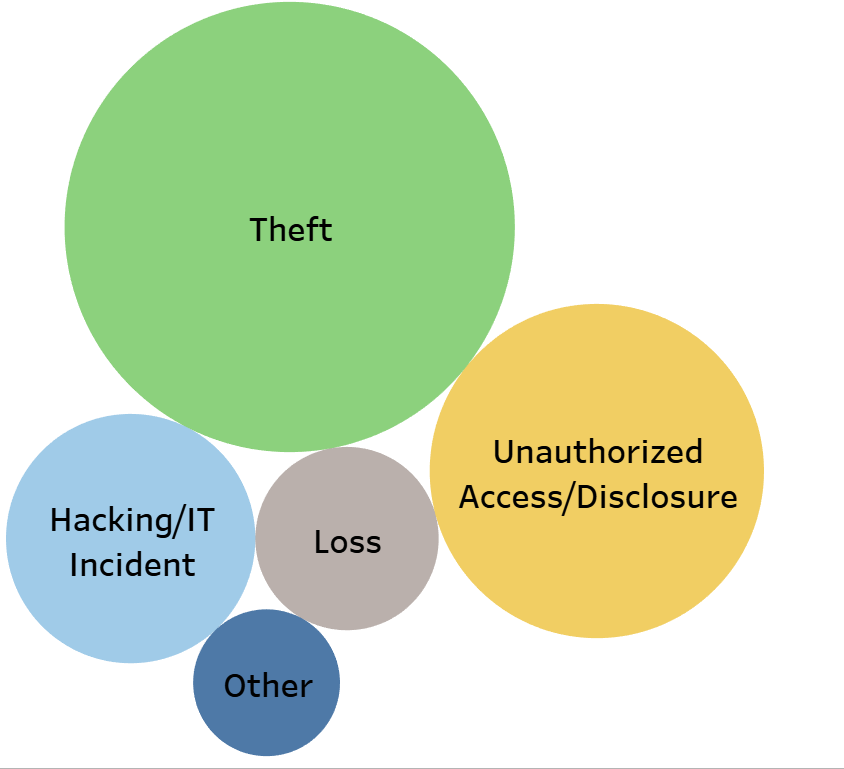
Data Source: https://data.world/health/health-data-breaches/workspace/file?filename=breach_report.csv
This bubble graph showcases the types of data breaches.
Surprisingly Hacking comes in third place, with Theft being the most common type of breach, surpassing all others by far.
Another widespread type is Unauthorized Access, and by which we mean people physically accessing confidential data without the means of hacking.
Source Of Compromised Data
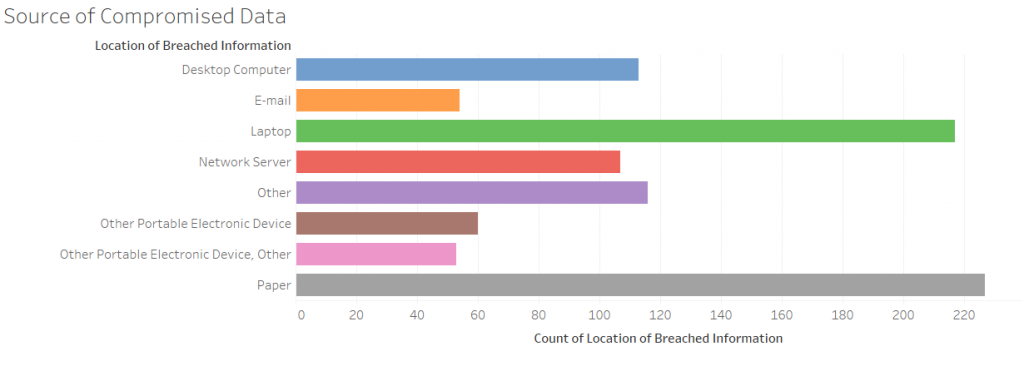
Data Source: https://www.kaggle.com/alukosayoenoch/cyber-security-breaches-data
This bar chart complements the one above since Paper and Laptops are the top 2 sources affected, which makes sense as Theft is the most common type of breach.
The Methods Used
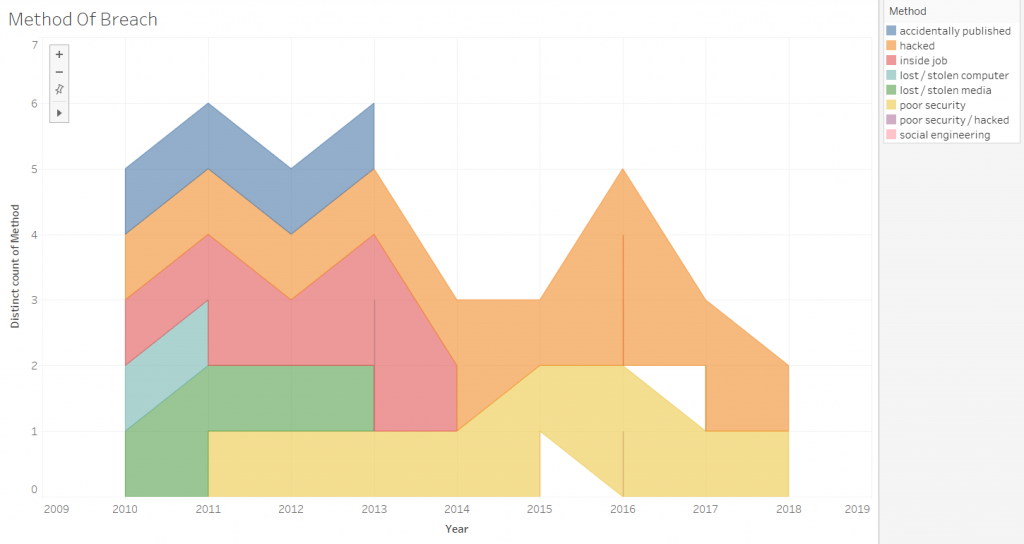
Data Source: https://www.kaggle.com/rileyrinidad/cyber-attacks-20102018#cyberattacks.xlsx
We can see the evolution of the methods used to breach data within the years. Clearly, hacking is starting to surpass other means in the most recent years. This is due to the evolution of technology thus companies switching from hard to soft copies stored on servers and clouds.
Passwords to avoid
A few years ago, a 10 Million combo (Username and Password) list was leaked on the Internet.
I wrote a script in Python that counts the number of occurrences of the same password.
And the results were the following:

Data Source: https://xato.net/today-i-am-releasing-ten-million-passwords-b6278bbe7495
Some of these results are pretty obvious, such as « 123456 », « password » or « 123456789 ».
These passwords are easily breached either by brute force or by a dictionary attack since they are known to be very common.
However, the 10th password was the most surprising.
If you look close enough, you can spot the word « dragon » in there, which is oddly funny.
Rule of Thumb
A password should always contain both upper and lower case letters, numbers and special characters. Also, one should never use the same password for different accounts as a breach in one could lead to all the accounts being stolen.
A nifty way is to come up with a pattern and apply it to all passwords. For example:
If I were to type « Data Breach » as a password, I would follow these steps:
- Start each word with a capital letter.
- Replace Latin characters with similar special characters (a->@).
- Separate two words with an underscore.
- Add a sequence of numbers that is easy to remember
I would then end up with a password like « D@t@_Bre@ch_Psswd1987 ».
A combination of these methods makes a strong password that cannot be brute-forced and its likeliness to be present in a dictionary is null.
Of course one should always make sure that his info remains secret and that temp mails are used on non-trusted sources whilst always using different passwords.
The Verdict

As we have already seen, data breaching is nothing recent, it has been going on for many years be it physically (Theft of papers and other belongings, Unauthorized access of documents or laptops) or digitally (Hacking).
As technology progresses, our devices are collecting more and more data, and it is only a matter of time until it is « mistakingly » published or breached by hackers. But either way, what was once private will be no more.
The Internet knows more about you than anyone else, and the only thing left to say is:


Fabulous, what a website it is! This website gives valuable
data to us, keep it up.