In order to improve the acknowledge of her employees about fraud behavior, fraud detection management used to analyze lot of data, the main goal of this department in any mobile operator call routing provider is to detect the behavior of fraudsters, from such analyze it becomes clear that fraudsters have high number of outgoing calls comparing to almost all normal users, also its rarely to find incoming calls on fraud number, since this SIM card is used only for fraud goals, one of the features that specialized fraudsters is the average call duration, its almost low, after analyzing lot of data it becomes clear that taking into consideration many features together is recommended, like considering the above mentioned features together, finally its important to notice how the fraudster uses same cell ID to make numerous number of calls, with comparison to normal user, how has higher number of used cell ID, in simple word, normal user has a ratio of changing cell ID over his outgoing calls greater than fraudsters, this article will illustrate fraud detection analysis using data from a mobile operator, I have the authority to use this data since I am doing an internship with an enterprise providing software solution for mobile operator.
The Role of Telecommunications in Business
Telecommunications is an important tool for businesses. It enables companies to communicate effectively with customers and deliver high standards of customer service.
Call routing in cellular network
Mobile Operators provide call routing through the traffic relay from the radio access network by the base station to the core network.
Call routing process is illustrated in the following figure:
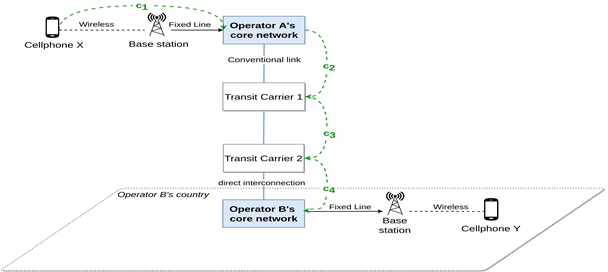
International off-net call scheme
Cellphone X calls Cellphone Y, a customer of operator B abroad. The originating operator (Operator A) transfers the call request through two intermediate carriers, with carrier 1 automatically chosen through least cost routing. Carrier2, with a direct connection, sends the traffic to operator B’s core network, which establishes the call route until cellphoneY.
Calls in VoIP networks:
Voice over IP (VoIP) is the technology used to transmit voice over wired or wireless IP networks. VoIP network is based on VoIP servers’ services to VoIP clients, and optionally VoIP gateways allowing interconnection with other telephone networks.
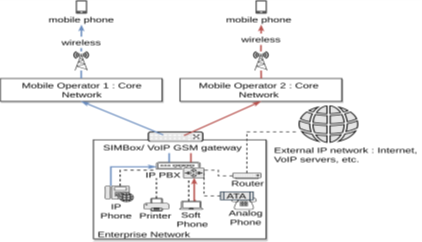
A SIMBox manages a set of SIM cards from various mobile operators to ensure the live broadcast of the audio signal from the IP network to the cellular one and vice versa.
The below figure depict how companies can use SIMBox as gateway from companies internal VoIP network to the cellular network:
SIMBox fraud schemes
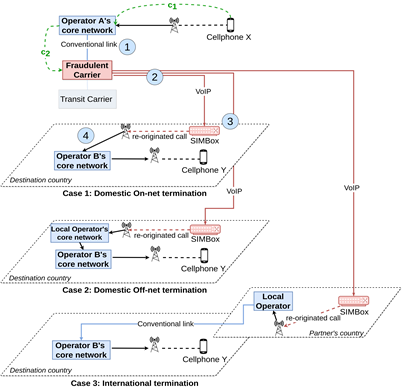
SIMBox fraud consists of deviating call traffic from the conventional routing routes to a VoIP network using the appropriate gateway, i.e., the SIMBox. Its scheme can be broken down into four steps:
The fraudulent carrier uses a gateway to route the traffic through the VoIP network to a country where fraudsters’ partners have a SIMBox, and the traffic is received at the SIMBox level.
The call re-originated by the SIMBox is terminated to the call recipient.
The below figure depict how fraudster intervene in the call routing in the cellular network:
Fraud detection management
Telecommunication companies used lot of methods to detect fraudsters, fraud detection management benefit from all the data collected over the network traffic to detect fraudsters.
Despite fraud detection management may hold some fraud SIM cards but the mission does not terminate at this point, the fraud detection management must analyze the data again based on the achieved results to improve its knowledge about fraudster behavior.
One of the combination of features that specifies fraudsters is the number of out-going calls with respect to number of incoming calls, in the following plot it’s obvious that fraudster usually have vast number of out-going calls and low number of incoming calls compared with innocent customers:
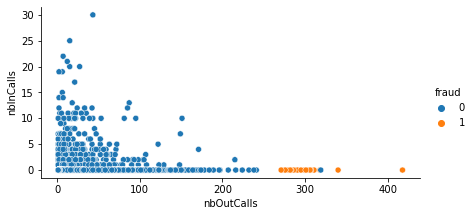
Of course, it’s not strange to find some non-fraud calling numbers that have also vast number of outgoing calls, this is since these calling numbers may be owned by special customers like marketing companies.
Indeed, classifying calling numbers with large number of outgoing calls as non-fraud customers depend on the data used by the fraud detection management, on the other hand this mean that high number of out-going calls is not enough to classify a calling number as fraud, but this is an important feature that must be taken into consideration.
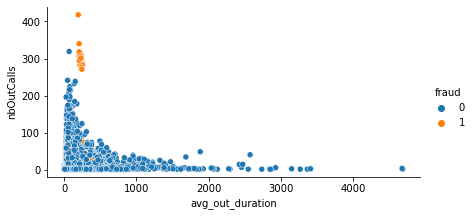
Another combination of feature that appears to be important is the average of outgoing calls with number of outgoing calls:
Its so clear that the fraudster almost has high number of outgoing calls, but their average out-going duration is not high, this can be explained by the fact that in many cases the calls that route through SIMbox used by fraudsters have bad quality.
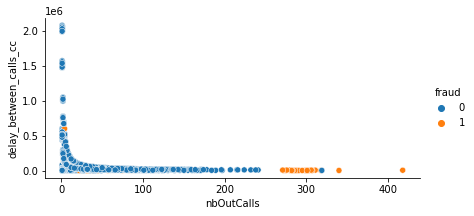
Another combination of the features that must noticed is the delay between calls with respect to number of outgoing calls, the normal user may make number of calls per day, usually these calls are distributed over the day, which mean that the delay between calls will be high in comparison with delay between calls for fraudster, the following plot illustrate this point:
Forth combination illustrated below:
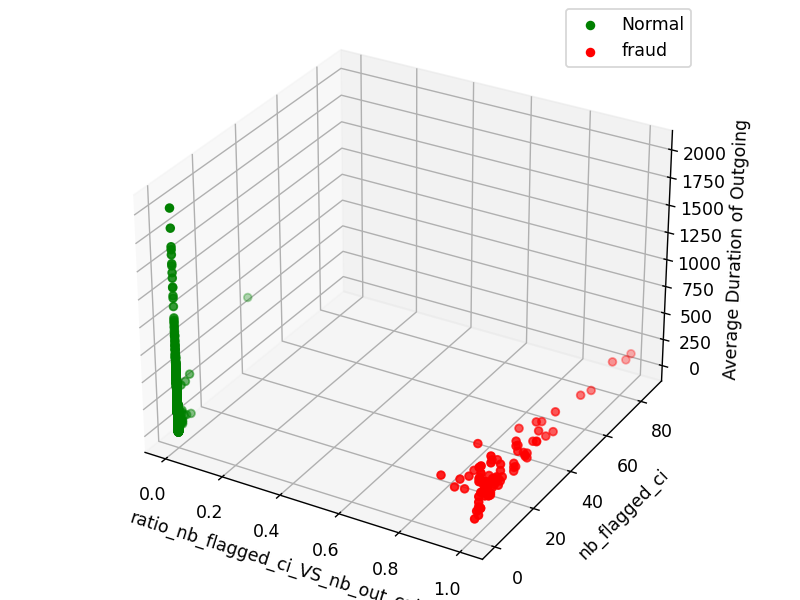
Flagged cell id are cell id that are used by fraudsters, the above plot shows that fraudsters (in red) used a lot of flagged of cell id, while other calling number didn’t, also its obvious that fraudsters have low high ratio between number of flagged cell id and number of outgoing calls, the most important point is that taking more features into consideration help in understanding the fraud behavior.
Another 3D plot used while analyzing fraud data is the following:

As the previous one, this plot gives fraud detection management clearer picture about the fraud behavior.
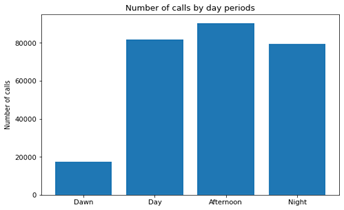
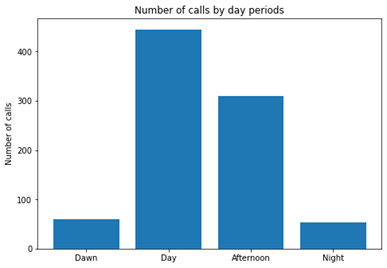
The following chart shows graphically how are the number of calls for normal users distributed over the day period:
Almost the calls are equally distributed from 12:00 to 23:59, while the same chart for fraudsters shows some different:
The last graph in this article tries to illustrate the connection between fraudsters and cell id, this network is very important to detect the area that fraudster is acting in, also to detect the most used cell id for geographical analyzes, also this type of graphs help us to detect communities in the cellular network:
Nodes in the center of each group are cell id and the nodes around are calling numbers using this cell id.
We can conclude from all the above graphs how fraudsters have typical behavior, and understanding this behavior helps us to improve our ability in fraud detection.